SSO - high level HOW-TO
What is it about?
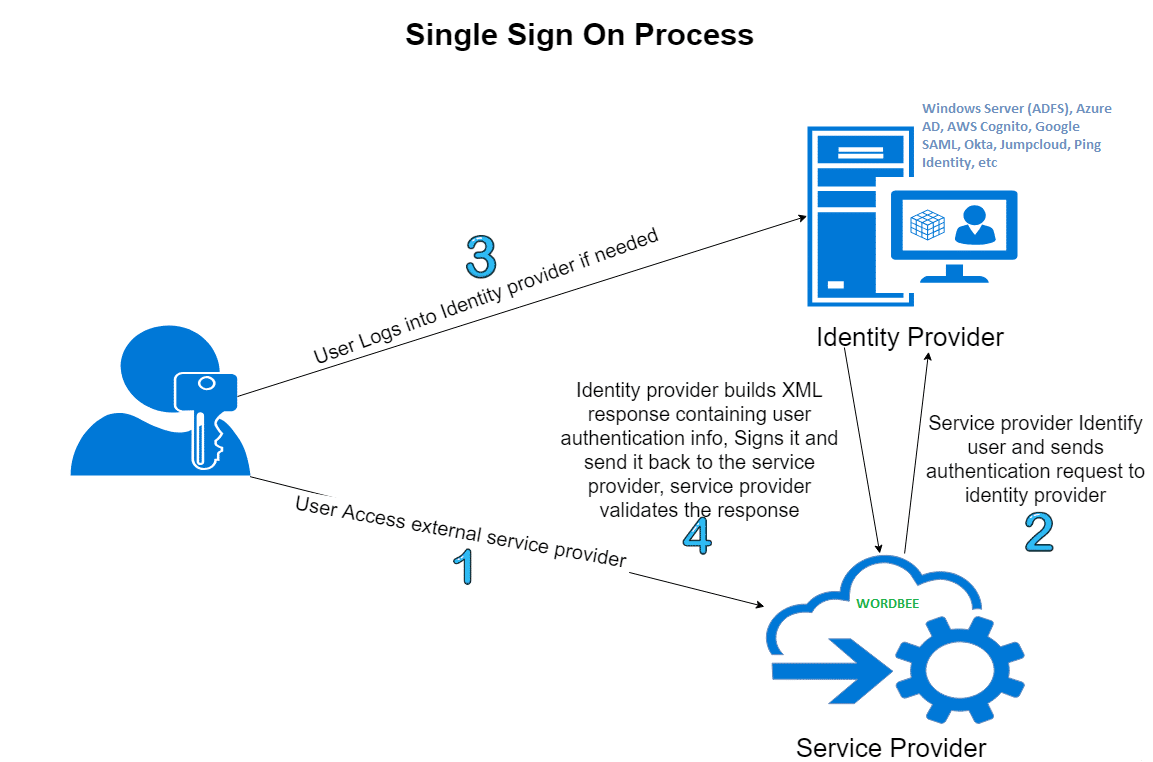
Long story short - SSO is for easier authentication process. Instead of maintening a local user database on the Wordbee platform it’s possible to use the centralized authentication system which you have in place. Here’s the high level diagram about how SSO authentication works. In our case, Wordbee platform is a Service Provider (SP), your centralized user database (Windows AD, Azure AD etc) is a Identity Provider (IdP).
As soon as SSO module enabled for your platform you will see an additional option for authentication on the login page
IMPORTANT NOTE: it’s only possible to integrate ONE IdP (Identity Provider) per platform, so you will not be able to use multiple authentication providers for the same Wordbee platform.
Why?
Easier user database managing and authentication
Sometimes you would need to create Wordbee platform local users and use SSO just for authentication and mapping to those existing accounts. But Wordbee SSO module can handle automatic user creation for you and then just take care about proper mapping.
Users passwords are secured
Users passwords are never stored on the Wordbee side. Wordbee SSO will always ask your IdP before allow user to be logged in.
How?
Here’s two main iterations to be completed in order to enable SSO for your Wordbee platform:
Create SAML instance config on your IdP portal using an information from Wordbee SAML metadata xml template.
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="wordbeesso">
<md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIDLjCCAhagAwIBAgIQvddBGjv55ZVKaSraksplgDANBgkqhkiG9w0BAQsFADAlMSMwIQYDVQQDExp3d3cud29yZGJlZS10cmFuc2xhdG9yLmNvbTAeFw0xNjEyMDIyMTU1MTVaFw0zOTEyMzEyMzU5NTlaMCUxIzAhBgNVBAMTGnd3dy53b3JkYmVlLXRyYW5zbGF0b3IuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAp71YEyYUnmoUoYbwNt3+rHYMH483RcaoATBu0KFJJzHztIaTTId4s/A+64eiJGdApKMIT4ztYL5RttHMcQsWxloelBjrRoUrlnLFMDQmtCWdjDwfymqWu3l6tp9Rtyzke9mqUOhlxeTMfVvpDgvZlseQg5Fje/Mxi54dKvg+c41say8/sdZRHmMMJFJSEg2OVuEZtGTkTidDyzh9eAq6sEHIsZWZyqp1SN2kUwQMlzhpiHmb94qZgQWcgz4Xe3k2ARrp/+x0FlOe48a0IvRIXCb7P3TKM0mozVXEe2rMC2ENDd5NGH9OBqT3gcbxrcMkdHpSz16sBMzn5FJxyqXDiQIDAQABo1owWDBWBgNVHQEETzBNgBCWONlDyBmdSbHcAp458uIXoScwJTEjMCEGA1UEAxMad3d3LndvcmRiZWUtdHJhbnNsYXRvci5jb22CEL3XQRo7+eWVSmkq2pLKZYAwDQYJKoZIhvcNAQELBQADggEBAJXpTTD3+c/lwgU9rVebPiyfOC96kmuIBPE7p8ScFhYqvbG2ydXhf9n+0SNYdgeGDCdaFUVmDfYsXBWSxFRVf5H5ZFZ1KtNFNPGnue7i8vQASK5NYwg2LU08lHm1AMtZdivIpl5QoQ+i1zY9e1cMFjEFSk5GB1bHKMuNd01e5xtYw4I0o6zLSLWaJqKhWqcrRZ4jzY7T8TumOmXCzgR4fZo4wXablZK8KnhSIBt9WfGfrUyB/O0eh6f/vdc2EhRTdDhWyhWmgIp3DhEMaCa7+BC1zdMlBGyfzTD7HJuT0zMiAaZbsqu0AadAxV1mo8PizgoXPyeD5X77+PDzd+9RHyQ=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://{{PLATFORM_DOMAIN}}/a/{{PLATFORM_NAME}}/Access/Logout.aspx"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://{{PLATFORM_DOMAIN}}/a/{{PLATFORM_NAME}}/Access/LoginFromExternal.aspx" index="1"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>Basically you need the entityID, SSO Login/Logout URLs and public certificate for SAML response encryption. Please just replace {{PLATFORM_DOMAIN}} and {{PLATFORM_NAME}} with your data (ask Wordbee support team if you’re not sure about a proper naming).
Get and share with Wordbee IT team the needed SAML settings
IDP name
SSO url
IDP certificate (signing)
Want response signed Yes/No
Want assertion signed Yes/No
Want assertion encrypted Yes/No
If you want to apply something special for user mapping and authorization it should be discussed separately with Wordbee DevOps team and then applied and tested.
If something went wrong…
Call Wordbee Support team or mail us on devops@wordbee.com
